Services
Services offer a way to provide programmatic, centrally-controlled, and consistent access controls for automated processes such as CI/CD pipelines and custom applications.

Any Resource that is defined in Twingate can be assigned to a Service, User, or both. This allows you to create consistent zero trust access controls across your infrastructure.
More specific details are described below, but the following summarizes the capabilities of Services in Twingate:
- Any Resource in Twingate may be assigned directly to a Service.
- Security Policies do not apply to Services, and instead, access is granted by a valid Service Key.
- Either the Linux or Windows clients may be run in “headless” mode to automate connection and access to Resources assigned to a Service.
Connector v1.0.30 or later is required
If you cannot add a Resource to a Service, you will need to update the Connector associated with that Resource first.
Service Components
- The Service This is the container object that is used to configure the Service. You can find Services under the “Team” tab in the Admin console.
- One or more Service Keys Service Keys are used to authorize access to all Resources assigned to a Service. Any Service Key that has not been revoked or has not expired can be used to access Resources assigned to a Service. Service Key expiration can be configured at creation time and expire after 365 days by default.
- One or more Resources assign to a Service. Any Resource defined in Twingate can be assigned to a Service.
Avoid overprovisioning Service Keys
Every Service Key on a Service Account will be treated the same at the API level, and overprovisioning may result in throttling or other issues. In situations where high-traffic systems need access to Resources, consider using a unique Service Account for each system.
Create a New Service
1. Navigate to Team > Services, and select “Create Service Account”

2. Select “Generate Key” to create a new Service Key
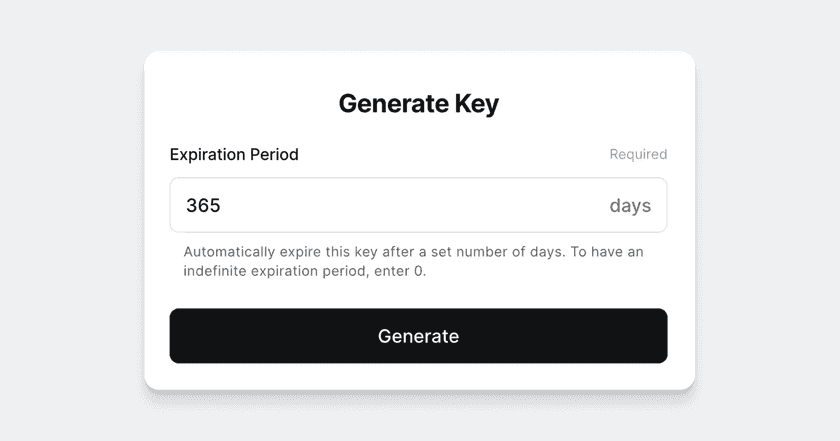
3. Save the new Service Key.
This is the only time that the Service Key can be viewed and copied.

4. Select “Add Resource” to assign Resource(s) to the Service.
Any Service Key authorizes access to all Resources assigned to the Service.
Service Key lifecycle
Valid Service Key states are summarized in the table below.
| State | Allowed Sections | Valid? | Notes |
|---|---|---|---|
| Active | Revoke Edit name | Yes | This is the default state for a new Service Key. Service Keys are only valid and usable when active. Service Key expiry can only be set at creation time; unlimited expiration is allowed.The Service Key’s name may also be edited while active. |
| Revoked | Delete | No | Service Keys must be revoked before they are deleted. Once revoked, keys cannot be made active again. |
| Expired | Delete | No | Service Keys expire automatically unless created with an unlimited expiration. |
| Deleted | N/A | No | Service Keys that are deleted are permanently deleted and cannot be recovered. |
Last updated 2 months ago